Protecting critical infrastructure in today’s threat-rich environment requires a portfolio of sophisticated solutions. Threats of all types jeopardize the nation’s security and continually evolve in complexity. In 2010, as the Arab Spring spread across the Middle East, monitoring social media quickly emerged as a new opportunity to identify such dangers, because social media often serves as a platform for people to express discontent. Terrorist groups are known to use social media to recruit and organize, or facilitate a range of other criminal activities that threaten global safety. Whether terror-related, a political uprising or an organized protest that could lead to civil disorder or criminal violence, monitoring social media is a valuable tool for law enforcement and intelligence agencies to protect society. While it is imperative that civil liberties be protected and that policy implementation guides be allowed to mature along with the technology, the use and application of social media monitoring is anticipated to grow.
Social media, of course, represents only a fraction of the overall threat information that is posed to critical infrastructure and event management. Digital evidence, criminal violations, signals intelligence and overseas encounters in theater with foreign fighters all represent critical datasets for protecting the United States. Historically, as threats evolve, the United States implements stopgap solutions to ensure security and safety is preserved. Over time, this approach results in a portfolio of fragmented solutions that must be sustained and often are not interoperable or efficient.
When putting emergency safeguards in place results in new stove-piped systems or applications, these emergency systems inevitably grow in complexity. Both cost to the overall security ecosphere and efficiency can be impacted. In a landscape where agencies are immersed in daunting collections of threat information, inefficient enterprise solutions increase liability. Too often, when tragedies occur, law enforcement investigations reveal that vital information, had it been known to exist, may have prevented an attack or mass casualty.
Since the September 11th terrorist attacks, one of the biggest concerns within the intelligence community has been information sharing. No agency wants to be liable for sitting idle on a critical piece of data that could have prevented a catastrophe. Security automation for facilities and events is a comprehensive concept that reduces these risks. SAFE reduces overall costs for sharing and exploiting information, enables disparate data to persist in the same environment and, most importantly, allows for near real-time alerts when danger warnings are detected. SAFE supports an enterprise approach to storing data and applying tools and analytics to reduce threats.
A SAFE Impact on Military Operations
Exploiting actionable intelligence from information posted on social media sites (such as Twitter, Instagram and Facebook) is a progressively powerful line of defense for protecting critical infrastructure, facilities and events.
In May 2015, Pentagon spokesman Col. Steve Warren confirmed an increased force protection at military bases across the globe. Warren stressed that this was not due to a specific threat but “a general increase in the threat environment.” [1] He later stated that this protective measure was in large part ordered in response to activity observed on social media. [2] Unfortunately, the threats posted to social media were identified too late during the recent terrorist attacks in Paris, France and Orlando, Florida.
The New York Times reported,
The gunman who committed the massacre at a popular gay nightclub in Orlando used multiple Facebook accounts to write posts and make searches about the Islamic State. “Now taste the Islamic state vengeance,” he declared, denouncing “the filthy ways of the west.” He even searched for references to the massacre while he was carrying it out …
And on Sunday morning, after opening fire at the Pulse nightclub and while a three-hour standoff with police was underway, “Mateen [the suspected gunman] apparently searched for ‘Pulse Orlando’ and ‘Shooting.’” [3]
Post-investigation techniques are no longer sufficient for managing the intelligence provided by social media. It is imperative that intelligence capabilities advance toward more preventive measures that can predict potential attacks and analyze trends of the data that is available within social media. Such advancements will protect critical infrastructure, soldiers and American citizens. Of particular interest is gathering and exploiting the facial data found in photos or videos – data that is potentially associated with profiles or posts of threatening information. Building upon social media exploitation, the SAFE concept can be implemented to deliver a Real-Time Surveillance and Exploitation Center for military operations.
The RT-SEC is a virtual environment, such as a cloud infrastructure, that serves as the central analytical platform for processing threat information that may contain faces. The RT-SEC considers specific data sources available to the Department of Defense that may contain faces. It also considers an aggregate of all the analytical services in corresponding legacy systems that provide protective intelligence to the military.
By implementing the RT-SEC, surveillance, as an example, can be enhanced to search against large datasets and provide near real-time actionable intelligence. The RT-SEC uses perimeter and mobile video cameras to alert DoD security personnel when suspicious individuals or activity is detected. By merging video, biometrics, identity intelligence and behavioral/pattern-of-life information, warfighters will be automatically notified of suspicious behavior or malign actors operating near DoD facilities. These warfighters will not need to rely exclusively on a match against the Biometric-Enabled Watchlist. The RT-SEC can operate in both communications-austere and communications- rich environments, depending on the operational need. Further, the RT-SEC
demonstrates scalability and can integrate camera and source inputs from multiple DoD facilities now and in the future.
How does RT-SEC work?
The RT-SEC ingests large quantities of photos and videos from a variety of intelligence sources, building a dynamic, searchable face database to support advanced analytics, site exploitation, and military action. The RT-SEC can manage multiple watchlists that can be defined with scalable sensitivity for thresholding and alert notification. The RT-SEC alerts can be routed to a warfighter’s
mobile device for immediate action, or automatically integrated into intelligence products for the Intelligence Command Center for adjudication. Existing DoD and intelligence command systems that provide identity intelligence do not aggregate across such a diverse collection. These collections, as previously described, evolved as the threats to the United States have grown exponentially. The RT-SEC offers the DoD a dynamic architecture that can keep pace with the comprehensive threat to the warfighter. It will model an infrastructure to expedite the dissemination of identity intelligence. The RT-SEC will also overcome the challenges that currently exist from stovepiped systems or capabilities requiring extensive human involvement to connect the faces encountered in the war on terrorism.
The RT-SEC leverages several proven technologies and best practices into an integrated capability. The infrastructure will control a suite of world-leading biometric technologies and host these tools within a cloud or similar virtualized environment. While each of these technologies independently proved to provide substantial investigative capabilities, this concept extends beyond any traditional implementations. The fully integrated suite of tools, combined with new business rules specific to the DoD, will exploit disparate data sources of faces and videos with unprecedented speed and accuracy. Additional technologies that augment the RT-SEC capability can be evaluated for subsequent integration to continually improve upon the critical infrastructure protection.
This identity intelligence capability can be achieved rapidly based upon the current state of these technologies, and it has the potential to directly assist in protecting the United States against the threat of terrorists and other enemies.
The RT-SEC will support and demonstrate a range of alert options. The end goal is to get alerts to the warfighter down-range at unparalleled speeds. Equally as important, the data that before would remain dormant or take extensive time to exploit can be made available to the forces in near real-time. These identity intelligence alerts or products will enable real-time decisions in special operations worldwide. The alert infrastructure will support command and control when adjudication or strategic operations are required (See Figure 1).
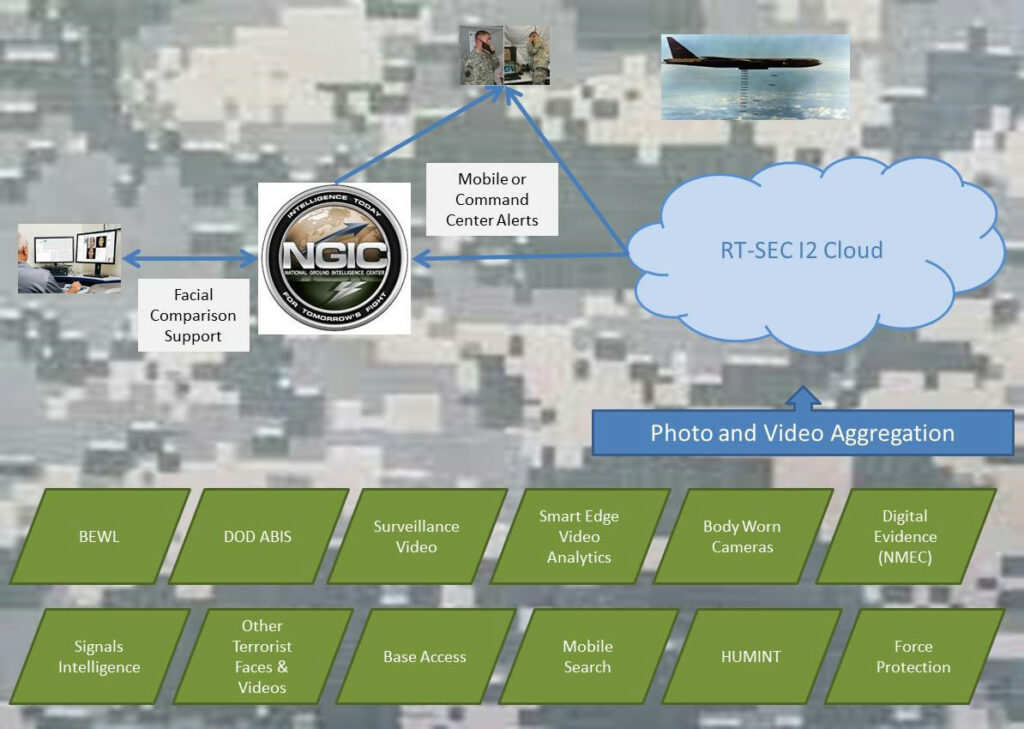
Figure 1: Illustration of the anticipated data sources that could be demonstrated in the RT-SEC proof of concept. (Released)
Figure 1 illustrates the anticipated data sources that could be demonstrated in the RT-SEC proof of concept. The overall concept could be demonstrated without operational data to prove the theory of SAFE. Whether the data is operationally relevant, or simulated, the information from these sources will be transmitted in large volumes to the RT-SEC Identity Intelligence Cloud or virtual environment. The video analytics and face recognition will occur in near real- time to generate the alert infrastructure. Data sources anticipated to be a part of the RT-SEC include, but are not limited to: the BEWL, representative data from Automated Biometric Identification System enrollments, surveillance video, information from the smart edge video analytics technology solution to support low-bandwidth constraints, body-worn cameras, representative data from the National Media Exploitation Center and Signals Intelligence, terrorist face archives from other sources, base access enrollments, mobile searches (such as smart phones or Handheld Interagency Identity Detection Equipment devices and human intelligence source data), and force protection generated information. Today, these DoD data sources have no way to co-mingle in a single environment to support near real-time alerts to the warfighter; but through RT-SEC this is made possible.
The RT-SEC Identity Intelligence Cloud concept is based on facial recognition from images and photos, but could easily extend to other technologies. For example, the solution could demonstrate the ability to detect movement in selectable areas, loitering, crowding, and occupancy counts. For vehicles, the solution could validate the ability to detect movement in a selected area; detect a vehicle crossing a line or tailgating; detect stopped vehicles; and perform speed analysis and license plate recognition. There are many promising advancements with video analytics, and the RT-SEC and SAFE concepts provide a framework to deliver these services to the warfighter. With the integration of more advanced analytics, the RT-SEC could demonstrate the ability to provide alerts on suspicious objects, protect assets, detect lights, and identify potential weapons. Collectively, the capabilities described with the RT-SEC concept are based on proven technologies. While facial recognition technology has not reached the maturity of fingerprints and DNA, it has been operationally proven to provide superior investigative proficiency. The RT-SEC pushes the technology to a new level. It provides an extensive safeguard for protecting military bases or other sensitive sites, demonstrating the ability to support a wide range of events that could pose threats to critical infrastructure.
SAFE Use Cases
Facilities and events are under constant pressure to increase their security posture. Methods for monitoring social media are rapidly progressing. Industry leaders not only deploy data aggregation and analytic techniques, but they use advanced linguistic interpretation to ensure threat information is fully interpreted and searchable in its native language. Likewise, this country has a comprehensive national screening solution comprised of the large-scale biometric systems at FBI, DHS and DoD. Each of these systems of record plays a critical role in keeping threats from entering the country, protecting the warfighter, or preventing crime.
The data used to support this mission, however, has broader applicability. For example, the biometric data of people who may be building improvised explosive devices should be shared with the correct personnel to help prevent their entry into critical infrastructure or to major events. Also, troves of threat information have been collected from signals intelligence and from digital evidence. Robust systems exist to collect and store this information, but exploitation must cut across multi-intelligence stakeholders. The DoD proof of concept for RT-SEC provides a detailed example of how SAFE streamlines security safeguards and permits an infrastructure to support the ever-evolving threats to our society. With the SAFE concept, it becomes possible to
understand that a person’s photo that was derived from digital media collected from the Osama bin Laden raid could send an instant alert to the National Ground Intelligence Center if that person tried to gain access to a military base or a Department of Energy facility.
In another use case, think about a detainee that was released from Guantanamo Bay and was subsequently linked by the Terrorist Device and Analytic Center to a latent fingerprint in an improvised explosive device that killed dozens of U.S. military troops. The goal is to ensure that the photo obtained from the detainee is available to support real-time surveillance at critical infrastructures worldwide, military bases, embassies and major events so it can be made actionable anywhere. While SAFE serves as a concept, the building blocks exist today to merge much of the existing face and video data and provide near real-time alert capabilities from live streaming surveillance video that searches across SIGINT, digital evidence, social media, and a range of other
critical information. These technologies have been implemented independently with great success and continue to be adopted within the U.S. government as well as commercially.
While sophisticated techniques improve our ability to monitor social media, there are still short-falls with the technology. Beyond stopping an imminent incident, the most critical capability to support the investigation is to identify people involved with planning or intending to execute the attack. Video and image data exist within social media, but it is currently not being leveraged. This information is often rich with identifying data that is otherwise unknown. Manual searching through this data is a daunting challenge, but video analytics and face-recognition automated technology offer a potential solution core to the SAFE concept. Facial recognition technology has the power to search millions of records within seconds, as demonstrated through large-scale biometric systems worldwide.[4], [5] The country of India, for example, has a national database that exceeds one billion records. SAFE can leverage this technology and exploit data in ways never before possible.
SAFE Summary
The SAFE concept fuses data that comes from social media and other threat information that comes from exploitation software (biometric modalities and items-of-interest images) with enhanced video surveillance data at a specific location to provide real- time actionable intelligence and vulnerability assessments. The enhanced video surveillance algorithms can be integrated into any existing facility that has a surveillance hardware infrastructure. With the software, users can rapidly customize alert features based on priority security needs of the facility and known local threat trends. The facial recognition feature cross-correlates between video data and social media pictures and video. The platform will be able to provide 1) predictive threat modeling based on historical data collected, and 2) real-time vulnerability assessments as threats are detected.
References
1. Martinez, L. (2015, May 8). Military Raises Security Status at US Bases Because of ISIS Threat. ABC News. Retrieved from http://abcnews.go.com/Politics/military-raises-security-status-us-bases-isis-threat/story?id=30902427 (accessed September 23, 2016).
2. Adl-Tabatabai, S. (2015). ISIS Threat Put U.S. Military Bases On High Alert. Retrieved from http://yournewswire.com/isisthreat-put-u-s-military-bases-on-high-alert/ (accessed August 16, 2016).
3. Blinder, A., Robles, F., & Prez-Pena, R. (2016, June 16). ISIS Threat Put U.S. Military Bases On High Alert. Retrieved from http://www.nytimes.com/2016/06/17/us/orlando-shooting.html?_r=1 (accessed August 19, 2016).
4. Altmann, G. (2016, May 18). Face recognition app FindFace may make you want to take down all your online photos. Retrieved from http://www.computerworld. com/article/3071920/data-privacy/face-recognition-app-findface-may-make-you-wantto-take-down-all-your-online-photos.html (accessed August 13, 2016).
5. Schroff, F., Kalenichenko, D., & Philbin, J. (2015). FaceNet: A Unified Embedding for Face Recognition and Clustering. IEEE Computer Society Conference on Computer Vision and Pattern Recognition 2015.


