“Cyber-Physical Systems of mission-critical infrastructure are susceptible to cyber-attacks, such as ransomware attacks Dependency on vulnerable Information Technology (IT) and Industrial Control Systems (ICS) of cyber-physical systems equates to an increased risk of threat exposure to a cyber-attack.”
Cyber-physical systems relate to mission-critical infrastructure systems affecting the physical environment, such as power, water, wastewater, safety controls. These systems have traditionally relied on physical security and necessary firewalls as access control. Cyber-physical systems have long technology refresh cycles of 20 years or more, which undermines the ability to address vulnerabilities with engineering upgrades. Extended refresh cycles present a complex system engineering challenge. There is an operational need for cyber defense capabilities to defend cyber-physical systems from cyber-attacks. Systems engineering principles were applied in the concept development of the Department of Defense (DoD) More Situational Awareness for Industrial Control Systems (MOSAICS) Joint Capability Technology Demonstration (JCTD) to convert operational needs into an engineering-oriented view for the development of a prototype.
The 8-star Letter
In February 2016, two four-star Admirals signed a letter identifying an operational need to defend the Department of Defense (DoD) mission-critical infrastructure. The letter subsequently was referred to as the “8-star letter” by a growing team of stakeholders. Sandia National Laboratories (Sandia) Critical Infrastructure Systems Department and the Naval Facilities Engineering Command (NAVFAC) Cybersecurity Technical Warrant Holder (TWH) responded in late 2016, with a concept to address the operational need by bringing the best of breed Department of Energy (DOE) Laboratory tools to the DoD, and named it “MOSAICS,” or More Situational Awareness for Industrial Control Systems (MOSAICS) (Scalco, R., Waugaman, B, Lacoste, J., Andrews J., Beary B., Roley R, 2018) [1].
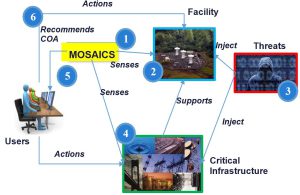
 The MOSAICS capability concept was to automate the exiting procedures to detect, mitigate and recover from a cyberattack, combined with the best of breed technologies related to analytics, visualization, decision support, and information sharing.
The MOSAICS capability concept was to automate the exiting procedures to detect, mitigate and recover from a cyberattack, combined with the best of breed technologies related to analytics, visualization, decision support, and information sharing.
Further system studies were performed that identified three initial MOSAICS capabilities: 1) an integration/operational capability to enable defense of control systems; 2) an ICS (Industrial Control Systems) baselining tool and Programmable Logic Controller (PLC) sensors; and 3) tailored visualizations, analytics, and automated cybersecurity orchestration. The latter was an emerging technology in the IT domain known as Integrated Adaptive Cyber Defense (IACD) developed by Johns Hopkins University Applied Physics Laboratory (JHU APL). IACD addresses the application of cybersecurity orchestration to the automation of cyber defense actions. A senior analyst supporting the U.S. Indo-Pacific Command (USINDOPACOM) Joint Innovation and Experimentation Division within the Requirements and Resources Directorate (J8) attending an IACD community of interest meeting proposed applying IACD principles to the MOSAICS initiative.
It took less than a few months for the concept of a cyber defense system for mission-critical infrastructure to be articulated into a proposal. As the needs analysis gained energy from stakeholders, the proposed approach was further developed in the form of a white paper that made its rounds through the DoD community. Early stakeholders in support of MOSIACS included Office of Secretary of Defense (OSD), NAVFAC, the National Security Agency (NSA), the Department of Energy (DOE), U.S. Cyber Command (USCYBERCOM), USINDOPACOM, U.S. Northern Command (USNORTHCOM), U.S. Air Force, and U.S. Marine Corps. Finally, in the spring of 2017, forces were joined with DOE and DoD labs forming what is now the MOSAICS team. The 8-star letter and this concept became the basis for the MOSAICS Joint Capability Technology Demonstration (JCTD), which commenced in 2018.
The purpose of an engineering Needs Analysis is to identify the needs – and the gaps between – where an organization is and where the organizational goals and priorities for resource allocation and business decisions lie. In this case, the Combatant Command wanted to be “left of the boom,” or in front of potential cyber threats to mission-critical infrastructure to avert threats. The challenge, or problem statement, was how to achieve cyber resiliency of mission-critical infrastructure through a cyber-attack.
Lifeline critical infrastructure sectors (e.g., water, power, and fuel), are commercial, privately owned entities, or known as existing “outside the fence.” This “inside/outside the fence” relationship inhibits the DoD’s ability to exert influence over the entire system network. The DoD, in most cases, does not produce power; however, it is highly dependent on power resources. Asset owners providing critical infrastructural support to the DoD are “outside the fence.” DoD assets reside “inside the fence,” which poses a complex challenge for the DoD’s ability to defend these critical assets since U.S. legislation and Title Authorities strictly define boundaries of how the DoD behaves with commercial industry and state, tribal and municipal entities.
Until recently, these OT systems were generally considered as being separated from cyber vulnerability by a complete disconnection, referred to as being “air-gapped” from other networks and the internet. For such a system, access control restrictions are behind firewalls. Digital technology innovations expose mission-critical infrastructure to an increasing level of connectivity, resulting in greater potential cyber vulnerability to the adversarial hacker kill chain. The need for systematic studies to address the wide attack surface required bringing together the expertise, including test engineers, as early in the process as possible—that is, before the JCTD kick-off meeting, and then throughout the different stages of the MOSAICS development. This process required close coordination with senior leaders to address policy constraints.
Early system studies revealed additional challenges for the MOSAICS team, particularly regarding the system boundaries. The Department of Homeland Security (DHS), designated as the lead federal agency to protect critical infrastructure for the United States against cyber-physical threats, identifies 16 critical infrastructure sectors as vital to the United States. This means those sectors “whose assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof,” (Department of Homeland Security, 2019) [3].
Smart Power Infrastructure Demonstration for Energy Reliability and Security (SPIDERS) JCTD
The MOSAICS team referenced other Science and Technology (S&T) efforts such as the Smart Power Infrastructure Demonstration for Energy Reliability and Security (SPIDERS) JCTD and the IACD framework, which is a design approach focused on speed and scale for cyber defense operations using secure orchestration. The team examined, for comparison and contrasting, predecessor systems such as IT systems, ICS, and Supervisory Control and Data Acquisition (SCADA) systems. Various methodologies were used to test and stretch the potential technologies under consideration to evaluate if the technology would meet or fail the requirements, and if the technology would make a significant cost difference in the solution, or potentially introduce new risk factors.
Sandia’s Computational Engine for Particle Transport for Radiation Effects (SCEPTRE) was identified as the test environment for the MOSAICS system. Lab Test 1 performed at Sandia informed the Measures of Effectiveness (MOEs), and subsequent design validation was performed to simulate and test the development of MOSAICS. A future lab test will be performed at the Expeditionary Warfare Center (EXWC), which is one of the target sites for the JCTD, and the final Military Utility Assessment (MUA) will be conducted during the Department of Navy (DON) Trident Warrior.
MOSAICS is a complex hierarchy of systems. It is the initial operational defense of mission-critical infrastructure.
Since MOSAICS is a JCTD, the “best” options were optimized for cost, schedule, and performance. Predecessor systems and essential building blocks were identified as system elements for a proof-of-concept, which would be verified and validated against the requirements. Elements of IACD, SCEPTRE, and Map-to-Model were integrated with key technologies at JHU APL (e.g., simulation, advanced sensors, Automation & Autonomy, analytics, Machine Learning (ML), security orchestration, customized human-machine interfaces, and visualizations). Ultimately, the tools and methodologies MOSAICS will deliver are an integrated MOSAICS tool suite, a control system cyber baselining tool, a design guide, and updated Unified Facilities Criteria (UFC) and a framework-based concept of employment. Subsequent systems engineering phases address other critical infrastructure sectors such as water, wastewater, fuel, and HVAC.
MOSAICS Operational Analysis
MOSAICS has turned out to be a complex hierarchy of systems. Initially, MOSAICS is intended to address the combatant command (CCMD) operational view “inside the fence,” which the DoD can eventually share with industry partners “outside the fence,” and commercial industry to further enhance and advance the technical capability. High-level goals were given to explain the system study objectives. The anticipated MOSAICS benefits are to meet an operational need and to enhance understanding of risk to critical infrastructure and supported operational capabilities. MOSAICS is intended to detect control system threats faster — from months to minutes; to improve situational awareness driving near-real-time decisions to enable faster cyber defender response, and to disrupt adversary kill-chain in mission-relevant time to limit adversary re-use of attacks through enhanced sharing of indicators and mitigations. It is the initial operational defense of mission-critical infrastructure.
Concept Exploration
From the start, MOSAICS leadership briefed senior leaders at the Pentagon, at Combatant Commands, and at the locations of critical industry partners during conferences to gain valuable community feedback. The JCTD process designates the Technical Manager (TM) as the leader among peers to bring the appointed Integrated Management Team (IMT) to an essential consensus. In the case of MOSAICS, a hybrid approach was designed by a Government TM at the Naval Information Warfare Center – Atlantic (NIWC – Atlantic) and a National Lab TM Sandia National Laboratories (SNL) to jointly guide the interactions. To realize the benefit of senior industry leaders, high group interaction involved all IMT members for problem-solving.
To realize the benefit of bringing advanced technology and commercial-off-the-shelf (COTS) knowledge to bear in the MOSAICS efforts, resident expertise in the technical areas of consideration was leveraged at the national laboratories for the operational domain knowledge to understand how advanced technology and COTS may be applied to the problem set.
Requirements Analysis
In the entire DoD, there is no other predecessor system like MOSAICS. Sandia performed a threat analysis of the requirements during the requirements analysis stage of the CCMD’s operational view. Pacific Northwest National Laboratory (PNNL) collaborated with JHU APL to perform site visits to clarify, correct, and quantify the requirements. The MOSAICS IMT ensured the consistency of documented requirements. Site visits resulted in the selection of the initial predecessor system. During the functional definition phase, the functional building blocks included threat capabilities, decomposed functions, and operational context. As potential threats were identified, and the functional capabilities of MOSAICS were further defined, a Security of Operations (SECOPS) was developed to describe how the system responds to the identified threat, and Use Cases drafted by the IMT Operational Manager (OM). The OM was also a hybrid approach with both USINDOPACOM and USNORTHCOM sharing the duty. The various technical teams were connected through the Joint Information Operations Range (JIOR) to allow for collaboration between the participating DOE and DoD labs.
The early planning focused on the system to be developed. Performing system-level studies helped the engineering team better understand the component capabilities. Pushing the limits to assess the operating range of every component helped further trace any failure that may be faced during the testing. Three critical activities for a system engineer that require technical knowledge to the component level are specifications requirements development, cost estimates, and the Analysis of Alternative (AoA)/trade-off studies. For the MOSAICS team, this component level expertise was critical. The MOSAICS systems engineers needed to probe into sub-component levels to effectively identify and discuss technical problems and component material solutions to meet the functional and physical specifications of the system design. They also assessed the technology readiness levels (TRL) to meet the best performance versus cost. Idaho National Laboratory (INL) and JHU APL performed a detailed survey of commercial tools. An evaluation of the technologies was performed to inform the physical definition phase.
Analysis of Alternatives (AOA)
It was important to the MOSAICS IMT to consider alternatives for feasible and attractive concepts for satisfying the requirements for this new system. Several alternative system concepts were examined before defining a set of system performance requirements. This AOA informed the potential for innovative technical approaches that featured advanced technology. It also avoided “the natural temptation” that “can easily preclude the identification of other potentially advantageous approaches based on fundamentally different concepts” (Kossiakoff, 2011) [4].
In the case of MOSAICS, Government-off-the-Shelf (GOTS) solutions were only considered to fill gaps recognized for cyber-physical integration with the intention of a research transition of MOSAICS to the commercial industry. The team performed substantial trade-off analysis to consider other alternatives before deciding which approaches to select for development because GOTS was deemed an unsustainable model. The research and development expense to create a GOTS solution was deemed too cost-prohibitive, and the time its application would have put the schedule at risk.
The MOSAICS team selected Sandia’s Map-to-model baselining tool because there was none other like it available for use on critical infrastructure. The down-select for other technologies was based on the cost against the requirements for “best” technology fit. The trade-off analysis was also essential before deciding which to select for development so that the commercial industry can participate in the future critical transition phase of the new system into the field.
Functional and Physical Architectures
Sandia’s SCEPTRE environment was used to better understand the functional aspects of the system, and to ensure that system components fit together and interact effectively to make up the total system (Kossiakoff, 2011) [4]. Mechanical components of MOSAICS were modeled in SCEPTRE at the PLC level along with the electrical interfaces and the IACD software components. To realize the MOSAICS physical architecture, a broad knowledge of disciplines in the development of complex critical infrastructure systems was leveraged. Domain expertise was again needed that extended through the system component level and across several categories in contract to the design specialist whose expertise and experience is usually within a single discipline.
The MOSAICS engineering team had to take multiple types of mission-critical infrastructure cyber-physical systems into consideration with different system design hierarchies. For example, a system design hierarchy for an electric power plant consists of a power plant generating station, and subsystems such as a transmission substation, made up of components such as transformers, and subcomponents such as turbines, further decomposed into parts such as the circuit breakers and switches. The electrical power plant system covers a considerable distance from the generating station to the end-user. This complex network makes cyber-physical systems susceptible to the cyber-attack kill chain.
Conclusion
In conclusion, there is an operational need for cyber defense capabilities such as MOSAICS to defend mission-critical infrastructure from cyber-attacks, which presents a complex system engineering challenge. Cyber-physical systems are susceptible to cyberattacks, and dependency on vulnerable IT and ICS equates to an increased risk of threat exposure, and certainly an increased threat surface area, to a cyber-attack. MOSAICS addresses an operational need for cyber defense capabilities to defend mission-critical infrastructure from cyber-attacks. The principal objective of the first phase of MOSAICS was the concept development phase of the systems engineering process to convert the operationally oriented view of the need into an engineering-oriented view required in the development of cyber defense capabilities of critical infrastructure. MOSAICS is anticipated to enter Military Utility Assessment (MUA) in the third quarter of FY21.
References
- Scalco, R., Waugaman, B, Lacoste, J., Andrews J., Beary B., Roley R, (2018). “More Situational Awareness for Industrial Control Systems (MOSAICS) Joint Capability Technology Demonstration (JCTD).” Retrieved October, 2019, from https://www.iacdautomate.org/may-2018-integrated-cyber.
- Scalco, R., Waugaman, B, Lacoste, J., Andrews J., Beary B., Roley R, (2018). “More Situational Awareness for Industrial Control Systems (MOSAICS) Joint Capability Technology Demonstration (JCTD).” Retrieved October 2019, from https://www.iacdautomate.org/may-2018-integrated-cyber.
- https://www.dhs.gov/cisa/critical-infrastructure-sectors
- “Critical Infrastructure Sectors.” Retrieved October 2019, 2019, from https://www.dhs.gov/cisa/critical-infrastructure-sectors.


